Data Governance - Security and Compliance Metrics
Understanding where data comes from, how it is transformed, and where it moves over time is vital for both compliance and data quality. This includes detailed histories of data sources, transformations applied, and downstream uses.Understanding where data comes from, how it is transformed, and where it moves over time is vital for both compliance and data quality. This includes detailed histories of data sources, transformations applied, and downstream uses.
Security and Compliance Metrics are essential components of a Data Governance Platform, serving as critical indicators of an organization’s adherence to security standards and regulatory compliance. These metrics are designed to provide a comprehensive view of the security posture and compliance status of data across an organization, helping to identify vulnerabilities, monitor for compliance with legal and policy requirements, and ensure that data protection measures are effective.
1. Access Controls and Audit Logs: Security and compliance metrics track who is accessing the data, when, and for what purpose. Audit logs are maintained to record all access and modification events related to sensitive data. These logs are crucial for forensic analysis in the event of a security incident and for regular audits. Access controls are monitored to ensure that only authorized personnel have access to sensitive data based on their role and requirements. These controls are done at the Data Object Layer using tradicional binlogs and point in time recovery, and also all KG Nodes changes are saved in the audit log, letting any DBA be able to revert to any point of time any changes in the Node level.
User & Profile management in AP.
2. Data Encryption Metrics: Metrics related to data encryption help ensure that data at rest and in transit is encrypted according to best practices. This includes monitoring the strength of encryption methods, the management of encryption keys, and the compliance with specific industry standards such as PCI-DSS for payment data or HIPAA for health information. At the AP level data encryption at rest is enabled by user demand in the momento of configuring the Repositories. We offer at the OS, Data Repository level and all communications are done thru encrypted connections.
3. Vulnerability Assessments and Penetration Testing: Security metrics include results from regular vulnerability assessments and penetration tests. These tests are conducted to identify and rectify security vulnerabilities within the organization’s IT infrastructure, including databases, applications, and network systems. Metrics gathered from these activities help in prioritizing security issues based on their severity and potential impact. We provide by user demand results of pen-tests and other important information about security to any customer.
4. Incident Response Metrics: These metrics track the organization’s ability to detect, respond to, and recover from security incidents. Key performance indicators might include the mean time to detect (MTTD) and mean time to respond (MTTR) to incidents. Effective incident response metrics are crucial for minimizing the damage from security breaches and for continuous improvement of the incident handling process. Any organization can use AP to track this incidents using our Data Platform for creating a custom Incident management data apps and generate crucial data insights for managing this issues.
5. Data Breach Metrics: In the unfortunate event of a data breach, these metrics detail the scope, impact, and nature of the breach. They include the types of data compromised, the number of individuals affected, and the breach's containment and mitigation efforts. These metrics are critical for regulatory reporting and for improving data security measures. Any organization can use AP to track this incidents using our Data Platform for creating a custom Incident management data apps and generate crucial data insights for managing this issues.
6. User Behavior Analytics: By monitoring and analyzing user behavior, security teams can identify anomalies that may indicate a security threat, such as unauthorized access or data exfiltration attempts. Metrics derived from user behavior analytics help in early detection of potential security incidents. At the AP level every KG Node has a detailed log of how data is deliverd thru all the Data Platform, helping users mitigate any un authorized access to data.
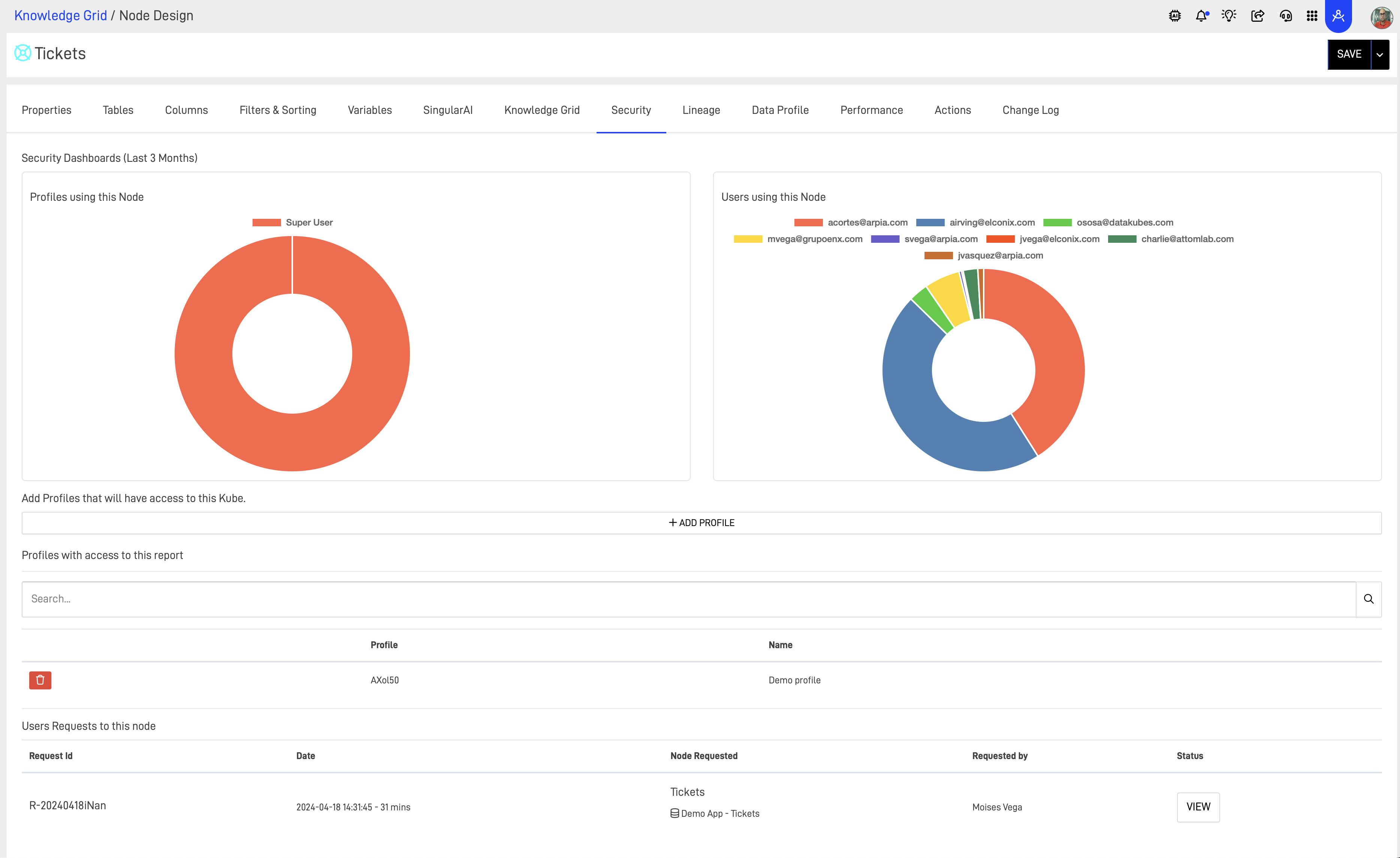
By continuously monitoring these metrics, organizations can effectively manage their security risks, ensure compliance with various regulatory requirements, and foster trust with customers, regulators, and partners.
Updated over 1 year ago
