Data Governance - Data Sensitivity Classification
Data Sensitivity Classification is a critical component of data governance that involves categorizing data based on its level of sensitivity, importance, and the potential risk associated with its exposure or unauthorized access. This process is essential for ensuring that sensitive information is adequately protected while still being accessible to those who need it to perform their duties effectively.
Purpose and Importance:
The primary purpose of data sensitivity classification is to prevent data breaches and ensure compliance with various regulatory requirements such as GDPR, HIPAA, and other privacy laws that govern personal and sensitive data. By classifying data, organizations can apply appropriate security measures and controls that correspond to the sensitivity of the data. This not only protects the organization from legal and financial repercussions but also helps in maintaining trust with customers and stakeholders.
Classification Levels:
Typically, data is classified into several categories, such as public, internal-only, confidential, and highly confidential, although these categories can vary depending on the organization's specific needs and the regulatory environment.
- Public: Data that can be made available to the general public without any risk to the organization. Examples include press releases, marketing materials, and published financial reports.
- Internal-only: Data that is not sensitive but is intended for use only within the company. This might include internal policies, training materials, and certain operational data.
- Confidential: Data that could cause damage to the organization if disclosed, such as business plans, financial records, or any information that provides a competitive edge.
- Highly Confidential: This includes any data that would likely lead to severe damage if exposed, such as personally identifiable information (PII), protected health information (PHI), security details, and legal documents.
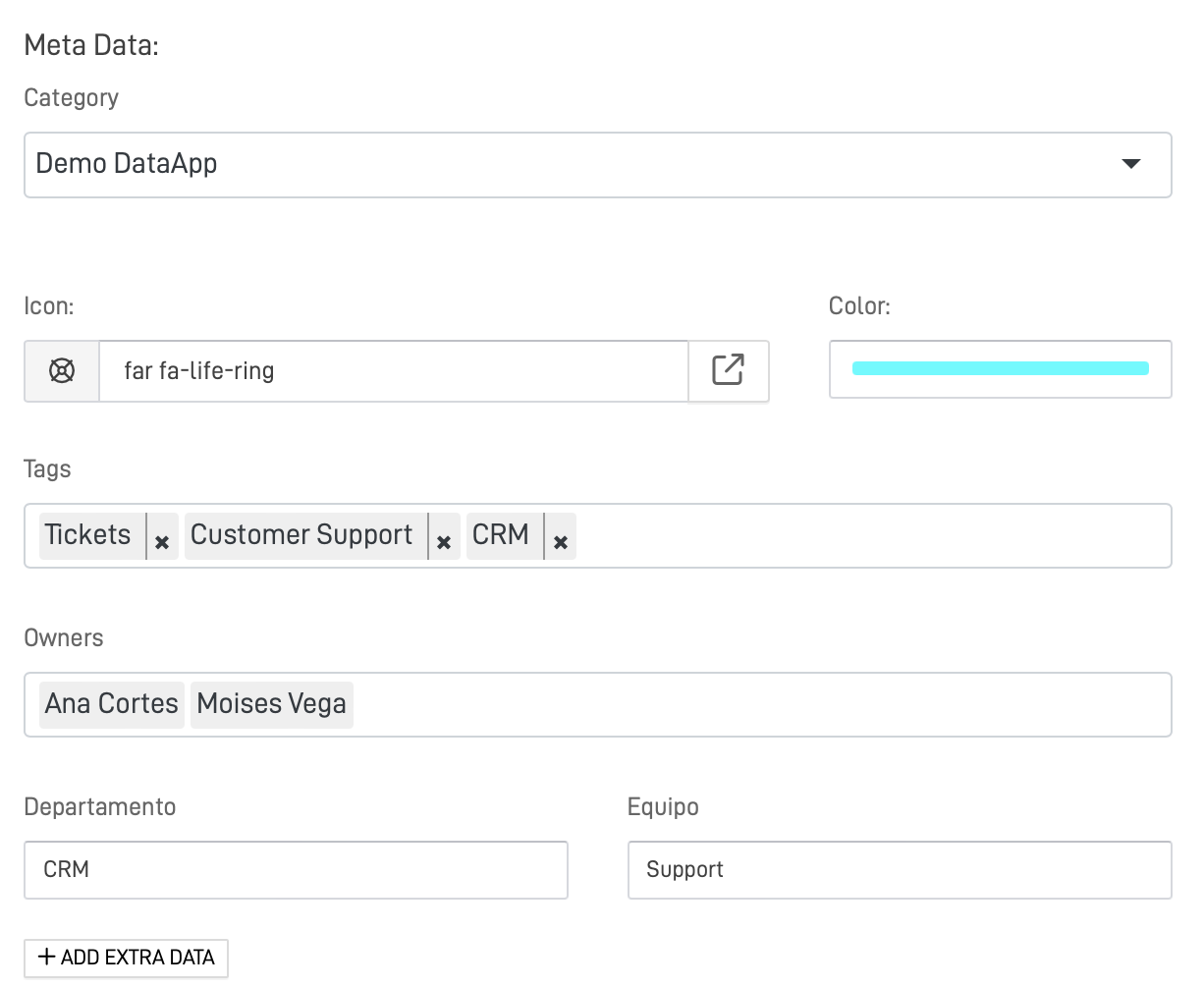
Meta Data on KG Nodes
Configure the classifications levels and term of usage of each KG Node is important for a good Data Governance.
Implementation and Access Controls:
Once classified, the data must be protected according to its classification level. This might involve encrypting highly confidential data, implementing access controls that limit data access based on user roles, or setting up audit trails to monitor data access and usage.
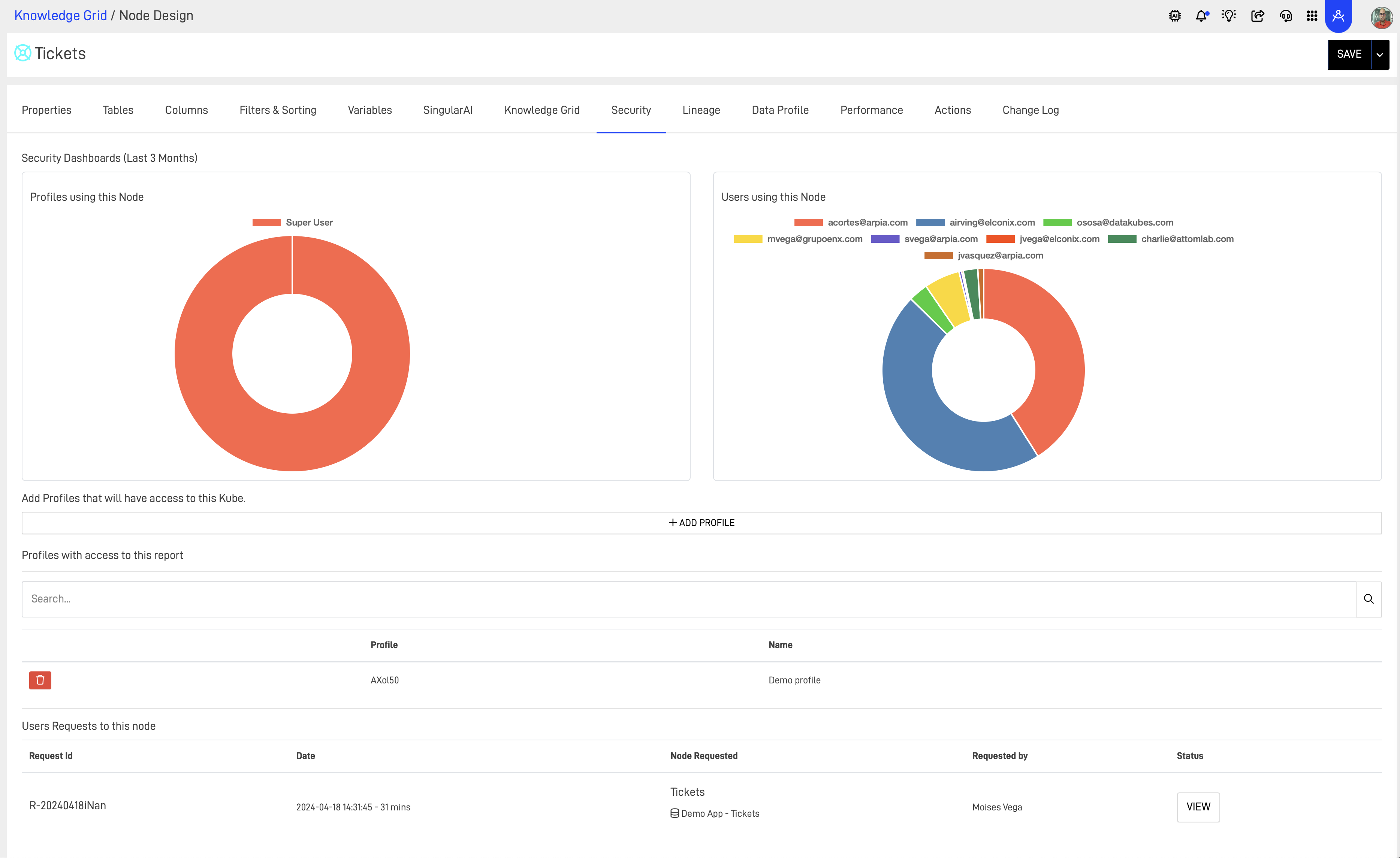
Our Security Tab on the KG node can show insights on users and profiles accessing the Node and User requests to this node.
Regular reviews and audits are crucial to ensure that the classification remains accurate over time and that the data protection measures are effective. As data changes, or as the organizational environment or legal requirements evolve, reclassification might be necessary.
A Data Admin can manage all these access controls using the security tools, user profile and KG Node security tab for managing what Users have access to data and how they use it.
Updated over 1 year ago
