Data Access Governance & Catalog Management
The Data Access Governance and Catalog Management (DAGCM) feature in a Data Governance platform provides a comprehensive and centralized data catalog for an organization, detailing all available data assets, including databases, files, and APIs. This catalog is equipped with advanced search capabilities, allowing users to easily locate and understand data through detailed metadata and previews. Users can submit requests for data access directly via the platform, where these are managed through an automated, customizable approval workflow, ensuring efficient handling based on the sensitivity of the data and the user’s role.
Key to this feature is its robust access control and monitoring system, which integrates seamlessly with existing identity management frameworks to enforce role-based access controls and maintain detailed audit trails of all activities. Real-time monitoring and automated compliance checks ensure that all data access adheres to strict security and regulatory standards. Additionally, data administrators have the ability to manually review and approve or reject data requests, especially those involving sensitive information, thereby maintaining high levels of data security and compliance while facilitating responsible data utilization across the organization.
Key Components of DAGCM:
Centralized Data Catalog
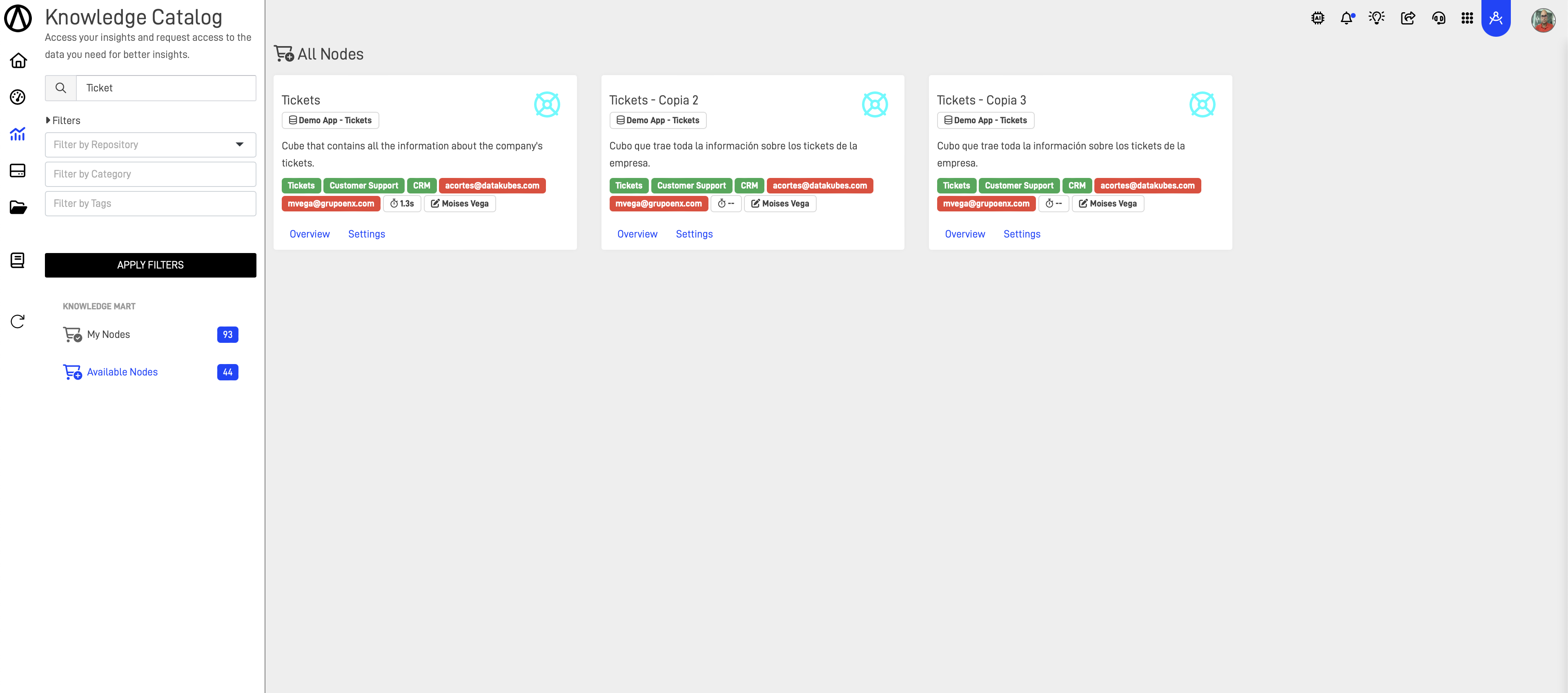
Comprehensive Inventory: Lists all data assets across the organization, including databases, tables, files, and even APIs. Each entry includes metadata such as data descriptions, data types, sensitivity levels, and usage guidelines.
Searchable Interface: Offers a user-friendly interface with advanced search capabilities that allow users to find data assets based on keywords, tags, metadata, and other criteria.
Data Preview and Sampling: Provides limited data previews or statistical summaries to help users understand the data without accessing the full dataset.
Data Request Management
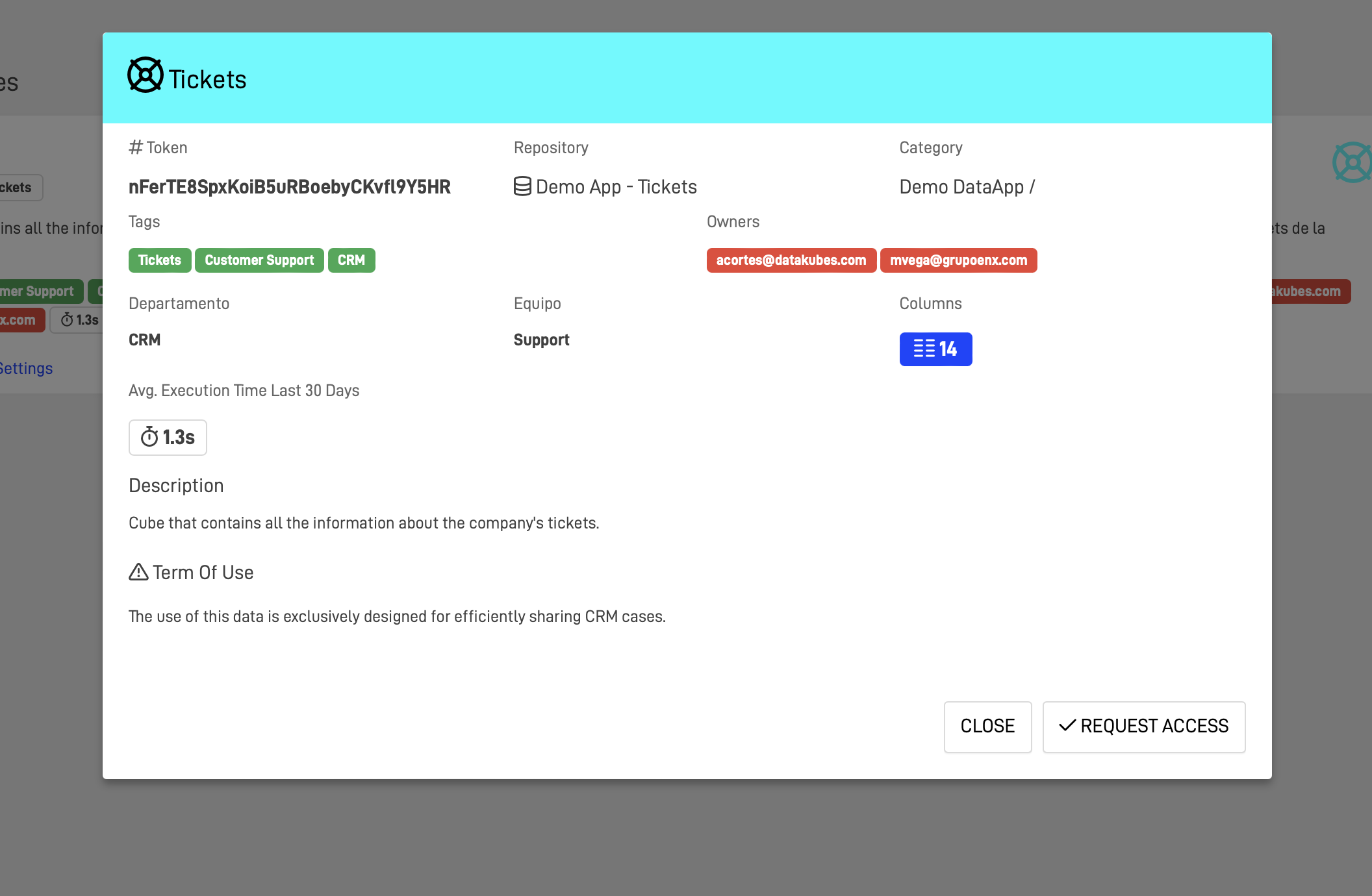
AP KG Node Requests are centralized.
- Request Submission: Enables users to submit requests for data access directly through the platform. Each request can specify the data needed, intended use, and duration of access.
- Automated Workflow: Automates the routing of requests based on data sensitivity and user roles. Includes notifications for approvers and feedback mechanisms for requestors.
- Customizable Approval Processes: Allows organizations to define approval workflows including multi-tier approvals for highly sensitive data.
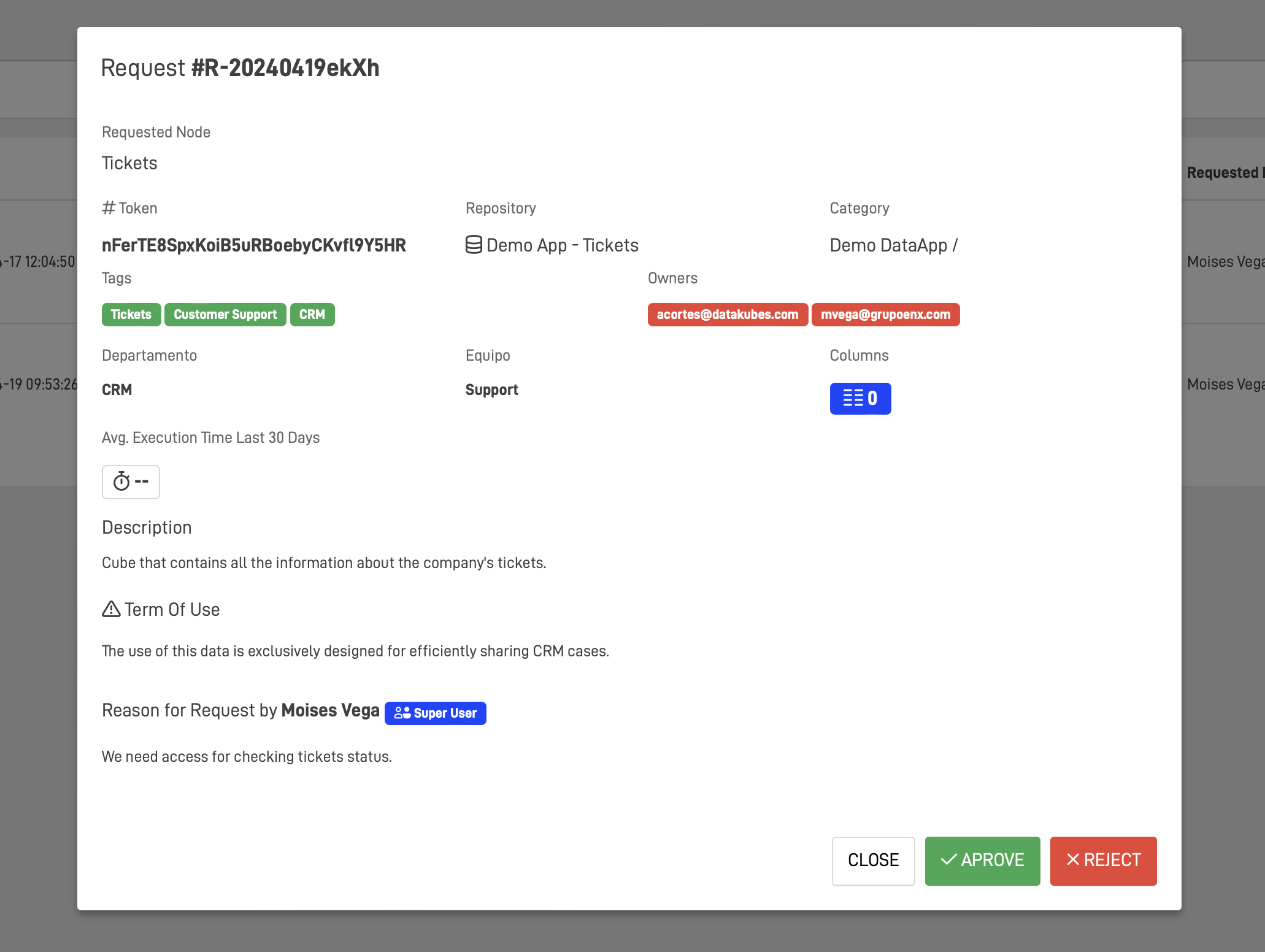
Access Control and Monitoring
- Role-Based Access Control (RBAC): Integrates with existing identity management systems to enforce access based on user roles and responsibilities.
- Real-Time Monitoring: Tracks all data access requests and usage, providing real-time visibility into who is accessing what data and for what purpose.
- Audit Trails: Maintains detailed logs of all data requests and actions taken on them, supporting compliance and forensic analysis.
Approval and Rejection Mechanisms
- Automated Rule-Based Approvals: Automatically approves or flags requests based on predefined rules, such as user role, data sensitivity, and compliance requirements.
- Manual Oversight: Allows data administrators or designated approvers to manually review and approve or reject requests, particularly when they involve sensitive data or deviate from typical use cases.
- Feedback and Communication: Facilitates communication between requestors and approvers through the system to clarify requirements, negotiate access levels, or provide reasons for rejections.
Compliance and Security Integration
- Compliance Checks: Automatically checks each request against compliance rules pertaining to data privacy laws (like GDPR, HIPAA) and industry regulations.
- Data Masking and Anonymization: Offers options to apply data masking or anonymization on sensitive data before access is granted, ensuring that privacy concerns are addressed.
Reporting and Analytics
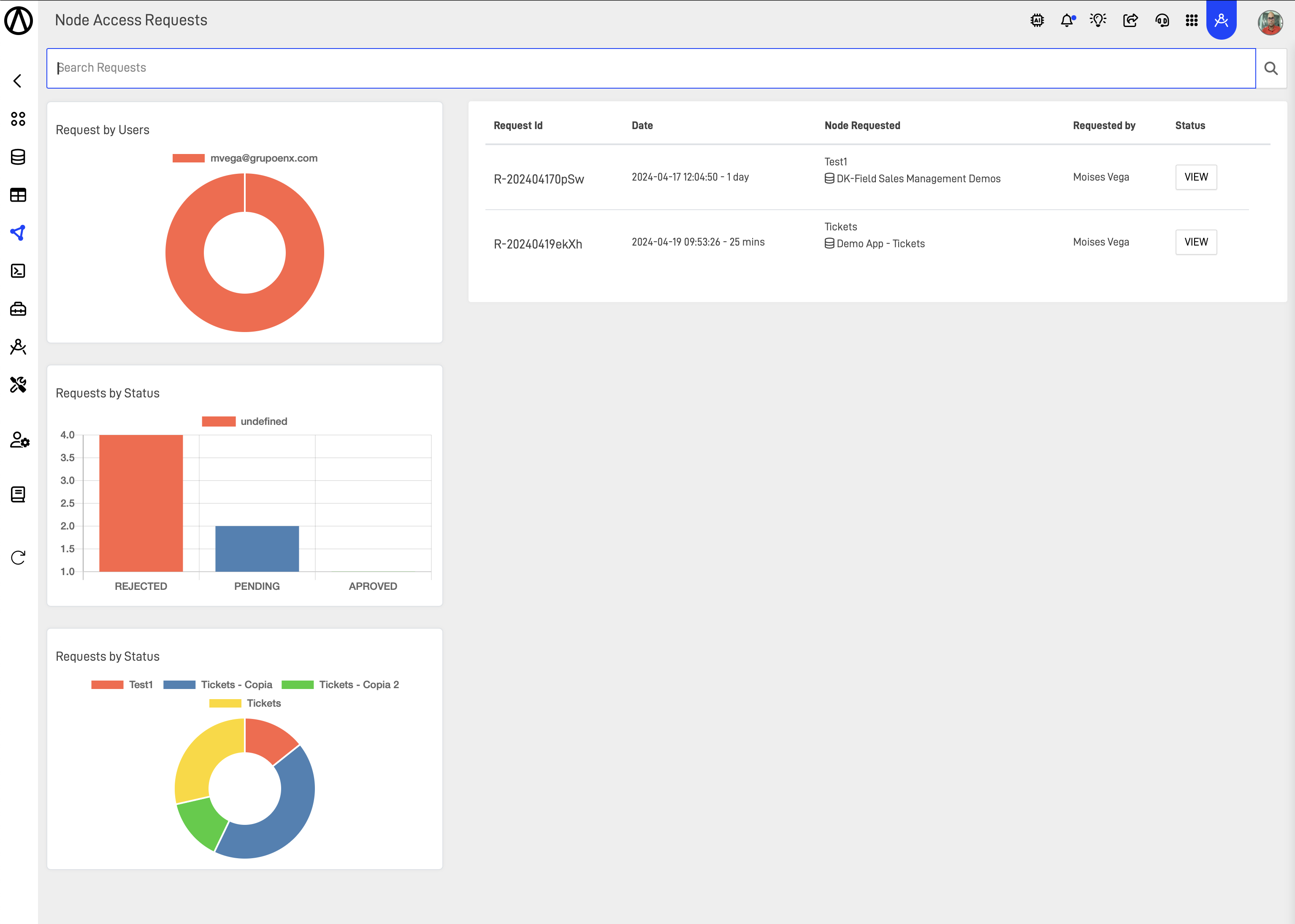
- Usage Analytics: Provides analytics on data request patterns, popular data assets, frequent requestors, and typical turnaround times for approvals.
- Compliance Reporting: Generates reports for regulatory audits and internal compliance reviews to demonstrate proper data handling and decision-making processes.
Updated over 1 year ago
